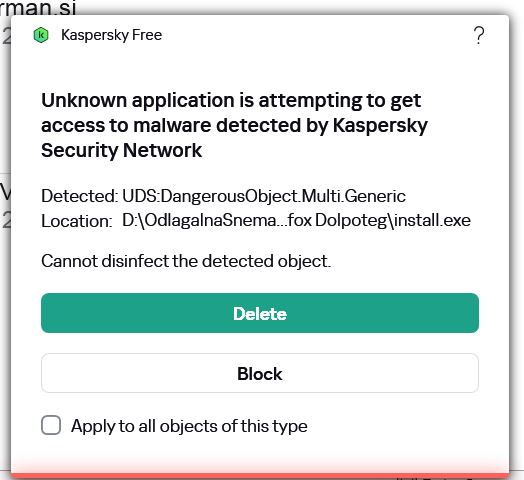
to bi pilo vodo ja...in da oseba lepo čaka, kdaj se bo trojanec "spet" pojavil online...problem je le v tem, da bi ti moral tisti, ki te hoče shekati, dati dotično kopijo...Morda so Windowsi pridobljeni iz kakšnega sumljivega izvora in že iso vsebuje trojanca. To je kar pogosto.
Kaspersky IS - zaupanje?
- Ustvarjalec teme dodo68
- Začetni datum
Uporabljate neposodobljen brskalnik. Ta ali druga spletna stran morda ne bo prikazana pravilno.
Posodobite brskalnik ali uporabite alternativni brskalnik.
Posodobite brskalnik ali uporabite alternativni brskalnik.
firmware običajno popravlja napake...in morebiti tudi kakšne varnostne popravke. ni nujno nekaj takega, da bi opazil razlike. običajno je dovolj, da imaš zadnji popravek. pa morda nastaviš, da lahko prideš na router samo z določene naprave (če sumiš lastno mašino, potem nastaviš ip od enega drugega domačega računalnika recimo...).To sem tudi jaz študiral da bi lahko bil prirejeni "firmware" na ruterju recimo.
Ni to neka draga zadeva da bi jo proizvajalec redno posodabljal.
Sem tudi poizkusil na novo dat gor firmware. Samo mislim da ni bilo nekakšnega efekta.
Pri firmware napadih gre večinoma za direktno periferijo, torej GPU, mrežna, programabilne miške/tipkovnice, razne druge USB naprave in ključki.To sem tudi jaz študiral da bi lahko bil prirejeni "firmware" na ruterju recimo.
Ni to neka draga zadeva da bi jo proizvajalec redno posodabljal.
Sem tudi poizkusil na novo dat gor firmware. Samo mislim da ni bilo nekakšnega efekta.
Primer: https://en.wikipedia.org/wiki/BadUSB
Hmm. Bom poskusil preverit.
Drugače pa mi je ta video dal malo za mislit:
Sem šel malo brskat po registru in našel cel kup japonskih/kitajskih/korejskih črk, ki sem jih kratkomalo zbrisal poleg pa tudi nekaj legitmnih programov:
UrpanVPN
Brave
Tor
itd...
Od kje so prišli ne vem.Jih pa sedaj več ni.
Sicer so exe bili preimenovani in posledično nisem bil pozoren v task managerju.
Hja bo kot kaže potrebno naredit fresh nov install.
Drugače pa mi je ta video dal malo za mislit:
Sem šel malo brskat po registru in našel cel kup japonskih/kitajskih/korejskih črk, ki sem jih kratkomalo zbrisal poleg pa tudi nekaj legitmnih programov:
UrpanVPN
Brave
Tor
itd...
Od kje so prišli ne vem.Jih pa sedaj več ni.
Sicer so exe bili preimenovani in posledično nisem bil pozoren v task managerju.
Hja bo kot kaže potrebno naredit fresh nov install.
Vsa zadeva pa ni bila brez posledic, kot kaže je bil del nekje v boot-u saj mi je po restartu kratko malo javil bsod da ne najde nekaj v boot-u.
Sem imel nekaj dela ampak sem spet v winsih. In čakam da se zadeva ponovi ali pa ne.
Nov install bo še moral malo počakati.
Tiste "hieroglife" pa sem dal v google translate pa ni najdel nobenega jezika iz katerega zna prevajati. Poskusil tudi ročno brez uspeha.
Tako da kot kaže ni kitajsko, korejsko, japonsko... ampak nekaj drugega.
Nekako bi razumel da bi to nekdo delal v času ko sem imel dostop do zelo hitrega interneta (1000/1000), ko so vsi meli 1 ali 10.
Ampak v današnjem času ? Ko je to nekak standard pa mi ni jasno zakaj.
Sem imel nekaj dela ampak sem spet v winsih. In čakam da se zadeva ponovi ali pa ne.
Nov install bo še moral malo počakati.
Tiste "hieroglife" pa sem dal v google translate pa ni najdel nobenega jezika iz katerega zna prevajati. Poskusil tudi ročno brez uspeha.
Tako da kot kaže ni kitajsko, korejsko, japonsko... ampak nekaj drugega.
Nekako bi razumel da bi to nekdo delal v času ko sem imel dostop do zelo hitrega interneta (1000/1000), ko so vsi meli 1 ali 10.
Ampak v današnjem času ? Ko je to nekak standard pa mi ni jasno zakaj.
Kaspersky ščiti tudi rusko vlado pred napadalci.
Na internetu se je znašlo 10 milijard gesel @ Slo-Tech
Na internetu se je pojavila datoteka rockyou2024.txt, ki vsebuje skoraj deset milijard edinstvenih gesel, ki jih ljudje dejansko uporabljajo. Datoteko je 4. julija na nekem hekerskem forumu objavil uporabnik z vzdevkom ObamaCare, v njej pa je v besedilni obliki (plain-text) zapisanih natančno...
Sicer 45gb fajl samo gesla so kot kaze prava.
Sem ze spremenil gesla, ceprav mi ni jasno kako so prisli do gesla od ruterja. Verjetno preko kaksne znane luknje...
Nic bo treba nekaj novejsega nabavit.
Mocno dvomim da ima kdo taksna gesla kot jaz, vendar nikoli ne ves.Pa je bilo geslo tako kompleksno, da ni možno, da bi ga uporabljal tudi kdo drug?
Sicer pa tega ni bilo tezko dobit ce imajo dostop do rač...
Vprašanje je samo kje so not prišli, in kdo, ter zakaj.
Logi so namreč "čudežno" izignili. Moram preverit če je kje kak skrit log...
Kaspersky zapira pisarne v ZDA @ Slo-Tech
Rusko podjetje Kaspersky Lab je zaposlenim v ameriški podružnici sporočilo, da jo bodo zaprli. Zaposlene bodo še ta teden odpustili, so za Zero Day povedali v podjetju. Gre za približno 50 zaposlenih, ki bodo prejeli odpravnine. Od 20. julija bodo začeli ugašati delovanje v ZDA, saj so ameriške...
Vsi av-ji, ki delujejo z ring 0 privilegiji lahko povzročijo bsod, oz sesujejo linux kernel.
Če bi kdo rad preizkusil zadnji kos programske opreme, ki je danes delala bsod reklamo
15 dnevni free trial
 www.crowdstrike.com
www.crowdstrike.com
EDR/XDR
 www.crowdstrike.com
www.crowdstrike.com
Če bi kdo rad preizkusil zadnji kos programske opreme, ki je danes delala bsod reklamo
15 dnevni free trial
Try CrowdStrike Falcon®
Take advantage of our free 15-day trial and explore the most popular solutions for your business. Try CrowdStrike free for 15 days!
EDR/XDR
What is XDR? Extended Detection & Response | CrowdStrike
XDR correlates data from endpoints, cloud workloads, networks and email, analyzes and prioritizes them, and delivers them through a single console.
Crownstrike tudi na linuxu dela težave
Crowdstrike did this to our production linux fleet back on April 19th, and I've been dying to rant about it.
The short version was: we're a civic tech lab, so we have a bunch of different production websites made at different times on different infrastructure. We run Crowdstrike provided by our enterprise. Crowdstrike pushed an update on a Friday evening that was incompatible with up-to-date Debian stable. So we patched Debian as usual, everything was fine for a week, and then all of our servers across multiple websites and cloud hosts simultaneously hard crashed and refused to boot.
Priporočila:
- Make sure you're running in user mode (eBPF) instead of kernel mode (kernel module), since it has less ability to crash the kernel. This became the default in the latest versions and they say it now offers equivalent protection.
Crowdstrike took a day to respond, and then asked for a bunch more proof (beyond the above) that it was their fault. They acknowledged the bug a day later, and weeks later had a root cause analysis that they didn't cover our scenario (Debian stable running version n-1, I think, which is a supported configuration) in their test matrix. In our own post mortem there was no real ability to prevent the same thing from happening again -- "we push software to your machines any time we want, whether or not it's urgent, without testing it" seems to be core to the model, particularly if you're a small IT part of a large enterprise. What they're selling to the enterprise is exactly that they'll do that.
Crowdstrike did this to our production linux fleet back on April 19th, and I've been dying to rant about it.
The short version was: we're a civic tech lab, so we have a bunch of different production websites made at different times on different infrastructure. We run Crowdstrike provided by our enterprise. Crowdstrike pushed an update on a Friday evening that was incompatible with up-to-date Debian stable. So we patched Debian as usual, everything was fine for a week, and then all of our servers across multiple websites and cloud hosts simultaneously hard crashed and refused to boot.
Priporočila:
- Make sure you're running in user mode (eBPF) instead of kernel mode (kernel module), since it has less ability to crash the kernel. This became the default in the latest versions and they say it now offers equivalent protection.
Crowdstrike took a day to respond, and then asked for a bunch more proof (beyond the above) that it was their fault. They acknowledged the bug a day later, and weeks later had a root cause analysis that they didn't cover our scenario (Debian stable running version n-1, I think, which is a supported configuration) in their test matrix. In our own post mortem there was no real ability to prevent the same thing from happening again -- "we push software to your machines any time we want, whether or not it's urgent, without testing it" seems to be core to the model, particularly if you're a small IT part of a large enterprise. What they're selling to the enterprise is exactly that they'll do that.